In today’s digital-first world, Australian businesses and government agencies face an unprecedented volume of data, much of it sensitive or confidential. The risks associated with mishandling this information are significant, ranging from regulatory penalties to reputational damage and national security threats. This is why Information Classification, Labelling, and Data Loss Prevention (DLP) have become essential pillars of modern information security strategies across Australia. At Business Aspect, we have developed a five-step methodology that we use with our clients to help them mature their use and protection of sensitive information.
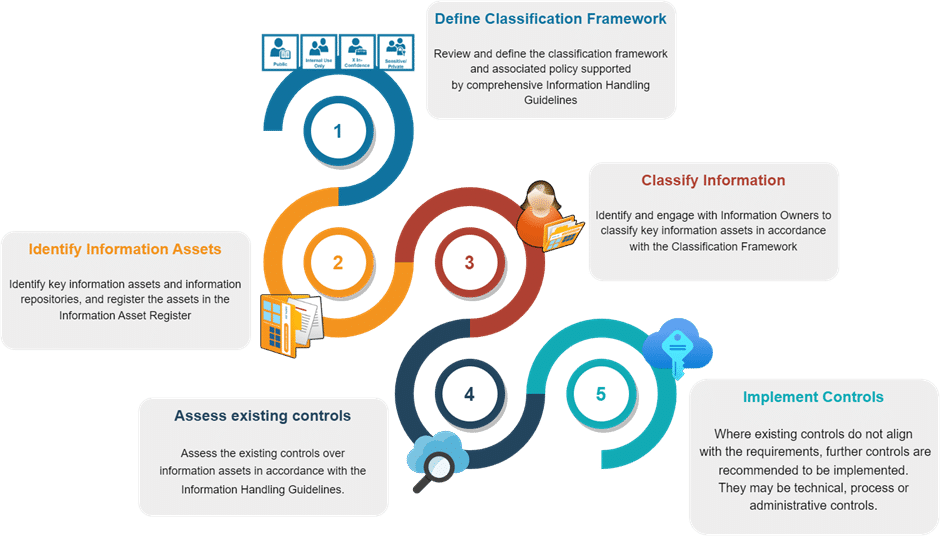
This article outlines each of the five steps and why they are important to ensure that your organisation develops best information protection strategies.
Step 1 – Define Classification Framework
Before any technical controls or security tools are implemented, the development of a comprehensive framework of policies, guidelines, and procedures is a crucial first step. This framework provides the foundation for consistent, effective, and compliant information management across the organisation.
A well-defined framework:
- Establishes clear expectations and responsibilities for all staff, ensuring everyone understands their role in protecting information.
- Aligns security practices with legal and regulatory requirements, such as the Australian Privacy Principles (APPs), the Privacy Act 1988, and industry-specific standards.
- Provides a structured approach for classifying, labelling, and handling data, reducing ambiguity and the risk of human error.
- Enables rapid response to incidents by outlining procedures for reporting, investigating, and mitigating data breaches.
- Supports ongoing training and awareness, helping to foster a culture of security and compliance throughout the organisation.
By starting with robust policies and procedures, Australian businesses and government agencies can ensure that their information security efforts are proactive, coordinated, and scalable as threats and requirements evolve.
Step 2 – Identify Information Assets
Before any organisation can effectively classify, label, or protect its information, it must first understand what data it holds, how it was collected, and where it is stored. This foundational knowledge is critical for several reasons.
First, knowing what data the organisation has allows it to identify which information is sensitive, confidential, or subject to regulatory requirements. Without this visibility, it’s impossible to apply the right level of protection or to comply with laws such as the Privacy Act 1988 or sector-specific regulations.
Second, understanding how data was collected is essential for ensuring that consent, purpose, and collection methods align with legal and ethical standards. This is particularly important under the Australian Privacy Principles (APPs), which require organisations to be transparent about data collection and use.
Third, knowing where data is stored—whether on-premises, in the cloud, or across multiple locations—enables organisations to apply appropriate security controls, monitor access, and respond quickly to incidents. Data sprawl and shadow IT can lead to unprotected or forgotten data, increasing the risk of breaches.
Step 3 – Classify the Information
Information classification is the process of categorising data based on its level of sensitivity and the impact that unauthorised disclosure, alteration, or destruction could have on an organisation. Labelling is the act of marking data with its classification, making it clear to users how the information should be handled.
For Australian businesses and government, this is not just best practice—it’s often a legal and regulatory requirement. Frameworks such as the Australian Government Information Security Manual (ISM) and the Australian Privacy Principles mandate the protection of personal and sensitive information. Proper classification and labelling help organisations:
- Identify and prioritise protection for their most sensitive data, such as personal information, financial records, or intellectual property.
- Comply with regulations like the Privacy Act 1988, the Notifiable Data Breaches (NDB) scheme, and sector-specific standards (e.g., APRA CPS 234 for financial services).
- Enable effective access controls, ensuring only authorised personnel can view or modify sensitive information.
- Facilitate secure data sharing within and between organisations, reducing the risk of accidental leaks.
Step 4 – Assessing Existing Controls
Before developing and implementing Data Loss Prevention strategies, it is essential to have a clear understanding of the existing soft (human and process-based) and technical (technology-based) controls within your environment.
Soft controls include elements such as staff training, security awareness programs, established procedures, and organisational culture. Technical controls encompass firewalls, encryption, access controls, monitoring systems, and other security technologies already in place.
Understanding these controls is important because:
- It helps identify gaps and overlaps in your current security posture, ensuring that DLP solutions complement rather than duplicate or conflict with existing measures.
- It allows you to leverage existing investments in security technologies and processes, making your DLP implementation more efficient and cost-effective.
- It ensures that DLP policies are aligned with how people work and the technologies they use, increasing the likelihood of adoption and compliance.
- It provides a baseline for measuring the effectiveness of new DLP controls and for continuous improvement.
- It helps avoid unnecessary complexity, which can lead to user frustration, workarounds, or even security vulnerabilities.
By thoroughly assessing both soft and technical controls, organisations can design DLP strategies that are practical, effective, and tailored to their unique risk environment.
Step 5 – Implementing Controls
Data Loss Prevention technologies and policies are designed to detect and prevent the unauthorised transmission of sensitive information outside the organisation’s boundaries. DLP solutions monitor data in use, in motion, and at rest, providing real-time alerts and automated responses to potential breaches.
In Australia, DLP is crucial because:
- Cyber threats are on the rise: Australia has seen a surge in cyber-attacks, including ransomware and phishing campaigns targeting both public and private sectors. DLP helps mitigate the risk of data exfiltration by malicious actors.
- Insider threats are real: Not all data breaches are external. Employees may accidentally or intentionally leak sensitive information. DLP tools can detect unusual behaviour and prevent unauthorised sharing.
- Cloud adoption increases complexity: As more data moves to cloud services, the risk of accidental exposure grows. DLP solutions provide visibility and control over data, regardless of where it resides.
- Reputation and trust are at stake: A single data breach can erode public trust and damage an organisation’s reputation, sometimes irreparably. DLP helps prevent such incidents before they occur.
Why Act Now?
Australia’s regulatory landscape is evolving rapidly in response to high-profile data breaches and growing public concern over privacy. The government is strengthening privacy laws, increasing penalties for non-compliance, and encouraging a culture of security by design. The 2023 amendments to the Privacy Act increased maximum penalties for serious or repeated privacy breaches, making robust data protection measures more important than ever.
Moreover, critical infrastructure sectors—such as energy, healthcare, and finance—are subject to additional obligations under the Security of Critical Infrastructure Act (SOCI). Information classification, labelling, and DLP are foundational to meeting these requirements.
Conclusion
For Australian businesses and government agencies, information classification, labelling, and data loss prevention are not optional—they are essential. These practices enable organisations to protect sensitive data, comply with legal obligations, and maintain the trust of customers and the public. As cyber threats evolve and regulatory scrutiny intensifies, investing in robust information governance is not just prudent, but is imperative for the security and prosperity of Australia’s digital future.
To get a concise understanding of your organisation’s maturity, please reach out to Business Aspect for a Sensitive Information Discovery exercise or if you wish to discuss further how we might be able to help.
If you would like to discuss how we might help you, please reach out to us.
